Reusing biometrics to allow secure access to an account or service.
Why
To identify return customers quickly and safely.
Common use cases:
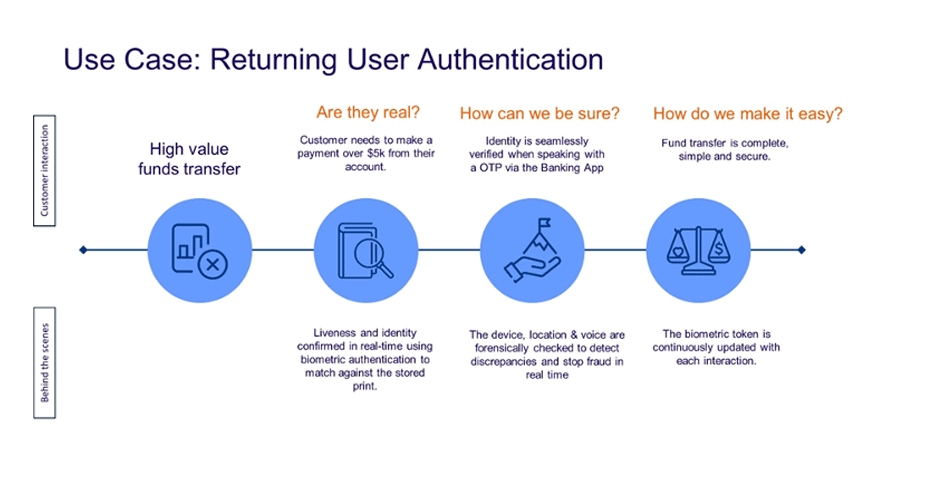
• Step-up Verification: Confirm high-risk transactions (e.g., large fund transfers).
• Streamline Logins: Reduce dependence on weak or cumbersome login methods.
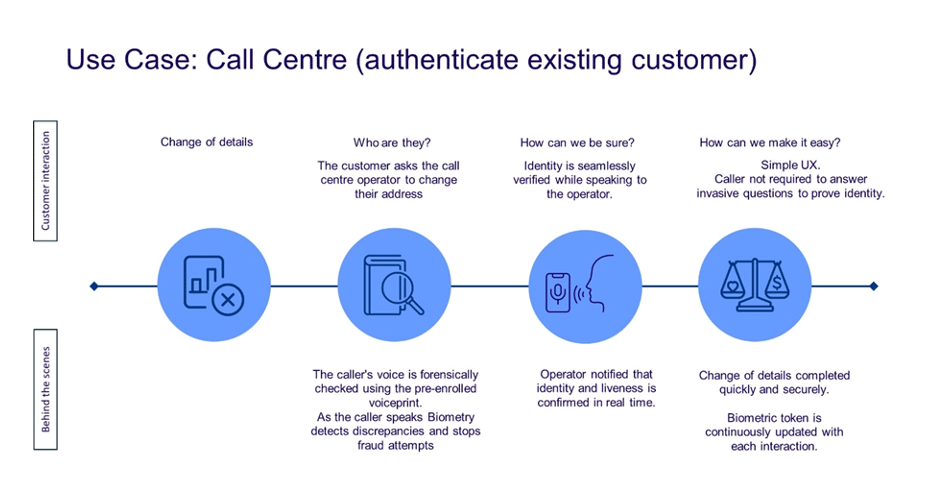
• Self-Service: Enable account changes (e.g., updating personal details).
Industries this is suited for
Banking, financial services, eCommerce, government, super, insurance, education, real estate, digital marketplaces—any sector with ongoing customer relationships.
Customer needs
• Simple Experience: Fast, easy access for legitimate users.
• Security: High accuracy and secure data storage to prevent fraud.
• Regulatory Compliance: Meet industry-specific regulatory requirements.
• Trust: No PII stored, reducing the risk of data breaches.
• Innovation: Adaptive solutions that evolve with new technologies.
How we solve this
• Multimodal Biometrics: Difficult to share or fake, providing stronger security.
• No PII Stored: Only a secure, encrypted biometric credential is created and used for comparison.
• AI-Enabled: Continuously adapts to detect new threats like deepfakes.
• Improved Login Process: No need for passwords, OTPs, or manual data entry—just seamless access.
• Compliance: Supports secure access across remote and mobile channels while maintaining regulatory integrity.
Benefits
• Fast & Accurate: Verify identities and access accounts in seconds with a high level of certainty.
• Secure: No personal data is retained, protecting users with encrypted biometric credentials that can’t be exploited by hackers.
• Trusted: Strengthen KYC processes for returning customers, block fraudulent attempts, and secure accounts against unauthorised transactions.
Journey Steps
- During onboarding, users may be asked for consent to store their biometrics.
- Once consent is given, Biometry securely stores an encrypted biometric template.
- When the user returns, they present their biometric for authentication.
- Biometry compares the new biometric to the stored template before granting access, ensuring a safe and seamless transaction.